Actually working on
- Coding interview
- Design systems interview
- Complete Linux Training Course to Get Your Dream IT Job 2020
- Mastering Docker - Fourth Edition
Here a collection of katas extracted from exercises and coding interviews.
Write a function that receives two strings and returns the number of characters we would need to rotate the first string forward to match the second.
For instance, take the strings “fatigue” and “tiguefa”. In this case, the first string can be rotated 5 characters forward to produce the second string, so 5 would be returned. Here are the step:
no rotations: “fatigue”
1st rotation: “efatigu”
2nd rotation: “uefatig”
3rd rotation: “guefati”
4th rotation: “iguefat”
5th rotation: “tiguefa”
If the second string isn’t a valid rotation of the first string, the method should return -1.
computes the number of rotations to make string first equal to string second, if possibile
first: String - string to be rotated
second: String - target string to be matched by rotating first
int - the number of rotations. If not possibile it returns -1.
You are provided a string containing a list of positive integers separated by a space ( " " ). Take each value and calculate the sum of its digits, which we call it’s “weight”. Then return the list in ascending order by weight, as a string joined by a space.
For example 99 will have “weight” 18, 100 will have “weight” 1 so in the output 100 will come before 99.
input: String - a string containing a list of positive integers separated by a space ( " " ).
String - a string with the values ordered by weight.
All numbers in the list are positive integers and the list can be empty.
“56 65 74 100 99 68 86 180 90” ordered by numbers weights becomes:
“100 180 90 56 65 74 68 86 99”
When two numbers have the same “weight”, let’s consider them to be strings and not numbers: 100 is before 180 because its “weight” (1) is les than the one of 180 (9) an 180 is before 90 since, having the same “weight” (9) it comes before as a string.
We are tracking down our rogue agent and she travels from place to place to avoid being tracked. Each of her travels are based on a list of itineraries in an unusual or incorrect order. The task is to determine the complete route she will take.
You are given an array of routes containing her travel itineraries. Convert this into a complete, in-order list of the places she will travel.
routes: List<String[]> - array of itineraries
String - An ordered list or destinations
All inputs have at least one valid, complete route
routes: [[“USA”,“BRA”],[“JPN”,“PHL”],[“BRA”,“UAE”],[“UAE”,“JPN”]]
return: “USA, BRA, UAE, JPN, PHL”
This is the first review I do about courses or lectures, they are mostly notes and personal considerations I hope you like it. I start with a live course from O’Reilly learing platform that I really appreciate, there are a lot of courses taken by famous people, try it if you can.
Michael is a regular contributor to the popular YouTube channel Computerphile, where his videos on topics such as image analysis, machine learning, and computer security have accumulated over 30 million views from people all over the world.
Here are some extracts and insights on the main topics.
In his introduction to encryption he talks about the power of the operator XOR.
XOR is a binary operator between two values that returns true if either one input or the other is true, but not both
Applying XOR twice reverse its effects: A ⊕ B ⊕ A = B
One Time Pad encryption use it as a bit mask with a one time password of the same length.
In symmetric cryptography the same key is used to encrypt and decrypt.
There are two typologies: stream cyphers and block cypers.
In stream cyphers you can encrypt long continuos streams. In a stream cipher, keys and algorithm are applied to each binary digit in a data stream, one bit at a time, rather than encrypting block of data.
The implementation is simple: each bit of the input is XORed with a one time bit key genereated from a pseudo random generator. A short password is used as a seed. “Pseudo random” means that it seems random but with the same seed it generates the same series of values. If the key stream output is random, then it will take a longer time for a crypt analyst to break it.
It is useful for movies because you can seek to any localtion of the stream and for devices where hardware AES acceleration is not available. An example of stream cypher is ChaCha20.
A block cypher takes a block of plain text bits and generates a block of cipher text bits, generally of same size. The size of block is fixed in the given scheme. The choice of block size does not directly affect to the strength of encryption scheme. The strength of cipher depends up on the key length.
Other primitives related treated are IVs, padding and block modes (ECB, CBC, CTR).
Here a simple explanation of how AES (Advanced Encryption Standard) works from his channel:
In asymmetric cryptography there are two keys envolved: a private and a public. You use the public key of the recipient to encrypt the message; only him can decrypt it with his private key.
RSA algorithm si used for generate public-private key pair. The keys (e, n) and (d) are reversible: either can be used for encryption, and the other used for decryption.
This leads us to two very useful use cases for RSA:
When we generate the keys the generate files will contains data like this:
—–BEGIN PRIVATE KEY—–
MIIEczCCA1ugA..AkGA1UEBhMCR0Ix
EzARBgNVBAgTC..0EgTHRkMTcwNQYD
……
It8una2gY4l2O..adsGeFKkyNrwGi/
7vQMfXdGsRrXN..HoX
-—-END CERTIFICATE—–
This format called PEM format is a text representation of the real binary key in DER format. We could store the binary version of the file only with DER encoding, but the most common way is the PEM version.
The Diffie–Hellman key exchange method allows two parties that have no prior knowledge of each other to jointly establish a shared secret key over an insecure channel. This key can then be used to encrypt subsequent communications using a symmetric key cipher.
Here two videos from his channel explaining Diffie-Hellman and the mathematics envolved
A hash function (in particular in cryptography) is any function that can be used to map data of arbitrary size to fixed-size values.
There are main characteristics of a good hash function:
Examples: MD5, SHA-1, SHA-2, SHA-3.
MD5 and SHA1 has been demoted from being a cryptographic hash function to a non-cryptographic hash function now.
When a signer electronically signs a document, the signature is created using the signer’s private key on the document hash. The resulting encrypted data is the digital signature. Who receives the document also receives a copy of the public key. If the public key can’t decrypt the signature is then considered invalid. The signature is also marked with the time that the document was signed. If the document changes after signing, the digital signature is invalidated.
Digital signatures use a standard format called PKI.
The PKI is the infrastructure that the industry created to manage the digital identities. The PKI created a hierarchical body of many organizations which their role is to issue digital identies. These organizations called Certificate Authority (CA) make sure that you are a legitimate company, and you are who you want to claim you are.
When you visit a website via a secure connection, the site sends a digital certificate to your browser. Your Internet browser compares the issuer with a list of trusted Certificate Authorities. If a match can’t be found, the client browser checks to see whether a trusted Root CA signs the issuing CA certificate. The browser’s chaining engine continues verifying the issuer of each certificate until it finds a trusted root or upon reaching the end of the trust chain.
SSL required the web server to have public key, and a digital identity, to give to the browsers. The industry decided to combine these two in one file, which is called : digital certificate, or SSL certificate. PKI policies defined the format for this certificate in a standard called X.509 that contains:
SSL is the standard protocol to secure the communication between a web server and a browser, by creating an encrypted link between the two.
When a browser hits the web server using the HTTPS protocol, it start the process. At the beginning, the encryption used is public-key encryption, which is an asymmetric type encryption. The web server has a couple of keys public and private. It sends the public key to the browsers, and the browsers use the public key to encrypt the communications later. Only the web server can know how to decrypt the communication. Because the public key decryption is slow and expensive, so the web server and the browser will switch to symmetric encryption where only one key is required. They negotiate between each other on what the best encryption algorithm they should use. The algorithm used would depend on the server and the browser. This negotiation phase is called TLS handshake.
I really appreciate this course, Mike Pound is an excellent speaker and he deals with those complex topics in such a simple way. In this three hour course he walks you through the fundamental components of encryption and in the end he combine those multiple primitives into an entire end-to-end system.
I’m moving a private knowledge base powered by WordPress to a public blog so I seized the opportunity to study a static site generator like Jekyll.
I chose Hugo one of the most popular generators, it’s really simple to use and to extend. Just download the CLI and run it in an empty folder and it will scaffold a basic site structure.
hugo new site quickstart
Then it’s time to download a theme, put it in the themes folder and set the config.toml file. I choose a theme named Soho.
To keep the theme updated I’m going to use a submodule as recommented by the quick start guide.
git submodule add https://github.com/alexandrevicenzi/soho.git themes/soho
Each theme has a lot of customizations that you can enable in the config.toml file.
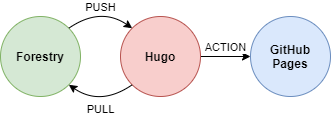
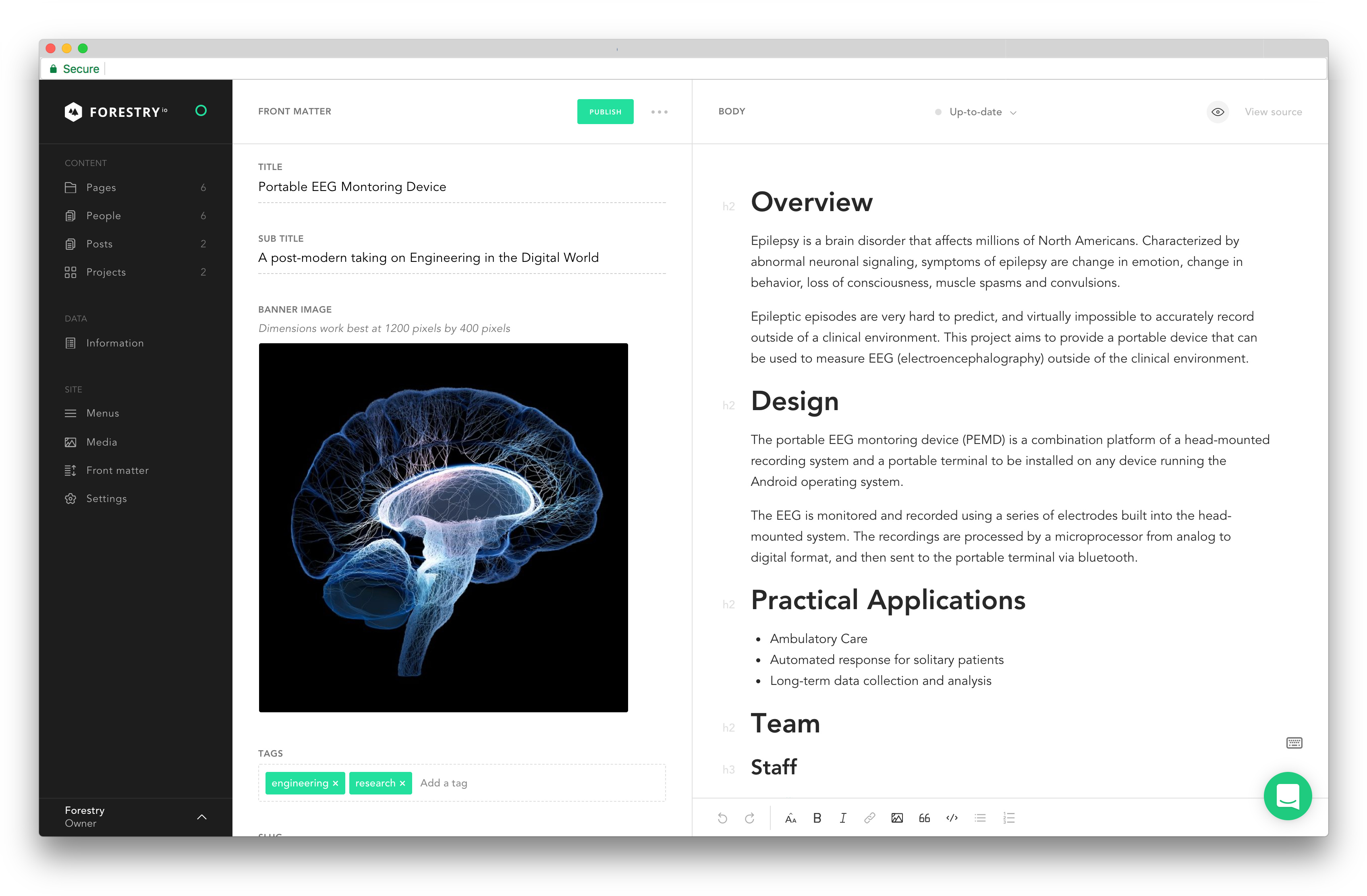
To manage contents in a web interface it comes in our aid Forestry.io: it reads data from a repository and let you edit pages easily, then it pushes back the changes keeping all synchronized.
GitHub Pages offers a static site hosting service for free available at https://<username>.github.io. Content is read from the master root folder of a special public repository under https://<username>/<username>.github.io.
I’m going to use two different repositories:
Every time I make a change on the private repository, I must commit on it, build the web site and then publish all the content to the public repository. This can be done in two ways: using git submodules or using GitHub Actions to automate the deploy; let’s try the second choice.
I’m gonna use an available action here to set up a CD workflow:
name: publish
# on every commit in the master branch
on:
push:
branches: [ master ]
jobs:
# it starts a job named build
build:
runs-on: ubuntu-latest
steps:
# it checkout the master branch and init/update the submodules (the themes)
- uses: actions/checkout@v2
with:
submodules: true
fetch-depth: 0
# it prepares the hugo command line on ubuntu
- name: Setup Hugo
uses: peaceiris/actions-hugo@v2
with:
hugo-version: '0.76.5'
# it builds the contents
- name: Build
run: hugo --minify
# it deploys the build on another repository
- name: Deploy
uses: peaceiris/actions-gh-pages@v3
#docs: https://github.com/peaceiris/actions-gh-pages
with:
personal_token: ${{ secrets.PERSONAL_TOKEN }}
publish_dir: ./public
external_repository: <username>/<username>.github.io
user_name: <username>
publish_branch: master
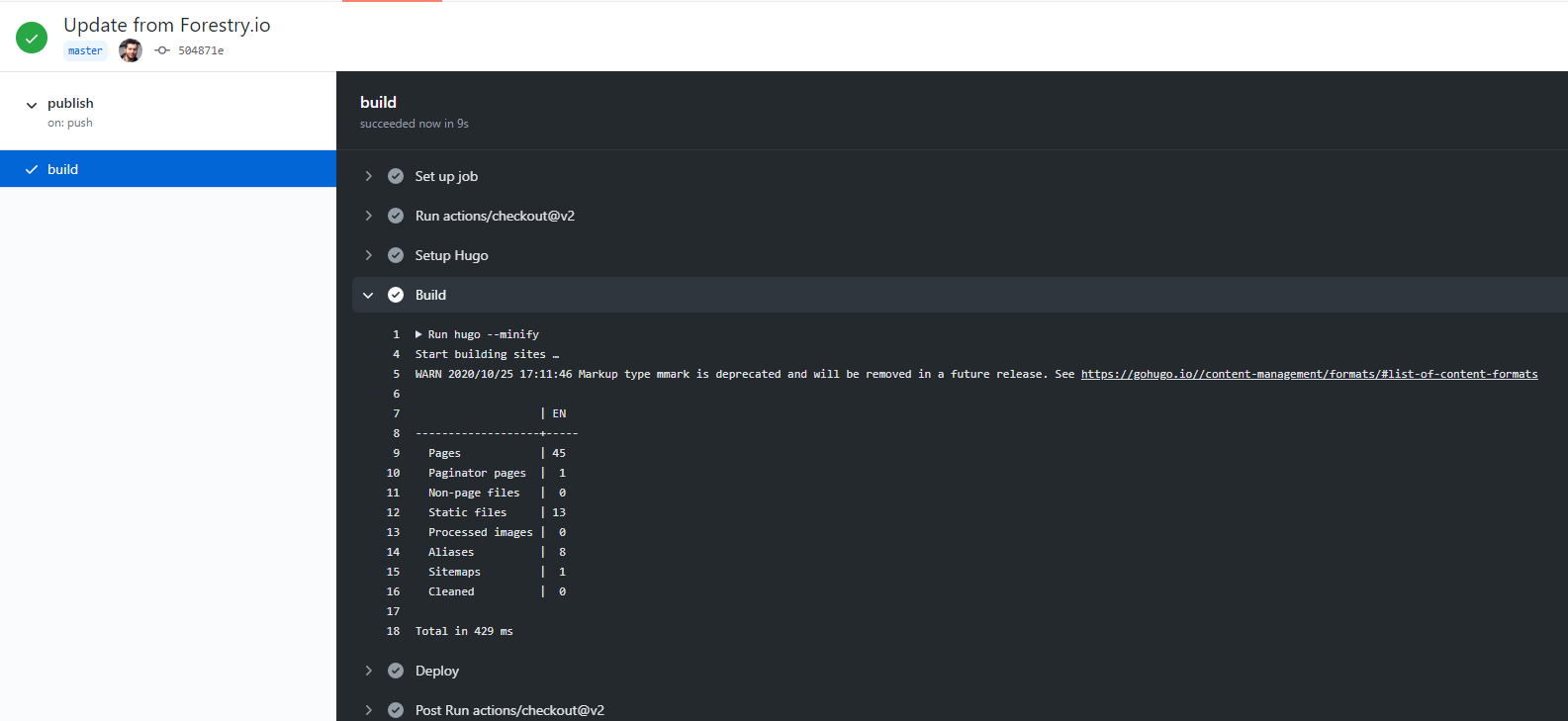
This task runs at every push:
Here’s an example of the workflow running:
Both repositories are under the same user so you can use a personal token to share permissions across them (another way is to use a deploy key).
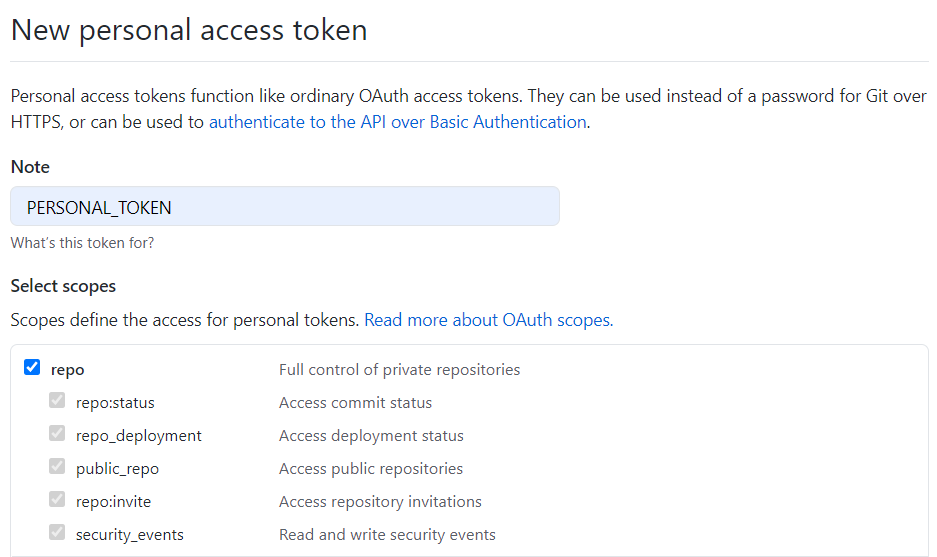
You must generate it and put the generated hash in the private repository secrets store so you can use it during the build like in the script example above.
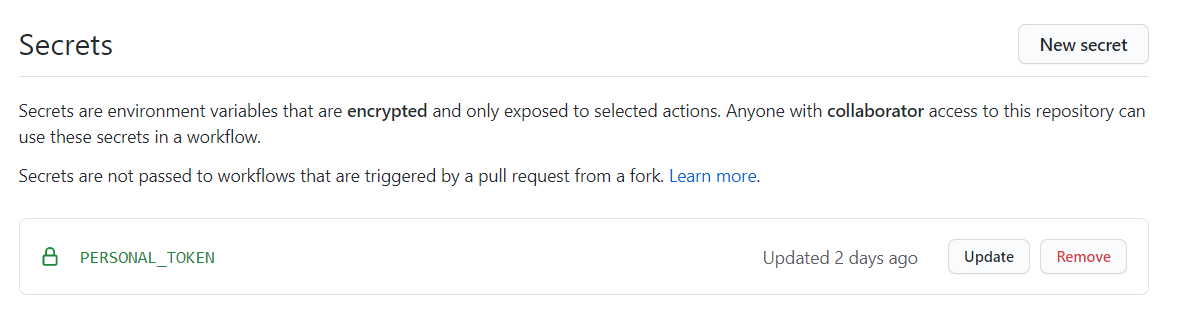
Now you can manage locally a simple markdown file and push it or you can do that online in a rich editor like Forestry and in a few seconds is available online.